Mitre ATT&CK!!!
In the ever-evolving landscape of cybersecurity, understanding the tactics and techniques employed by cyber adversaries is crucial for organizations to fortify their defenses. One powerful resource that has gained prominence in recent years is MITRE ATT&CK.
What is MITRE ATT&CK?
MITRE ATT&CK, short for Adversarial Tactics, Techniques, and Common Knowledge, is a globally recognized knowledge base developed and maintained by MITRE. It provides a comprehensive framework that catalogs real-world cyber adversary behavior and their tactics across various stages of a cyber attack, from initial intrusion to post-exploitation activities.
Structure of MITRE ATT&CK:
-
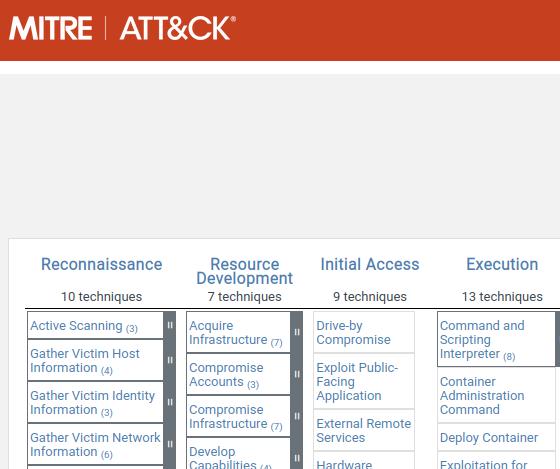
Tactics: MITRE ATT&CK is organized into multiple tactics that represent the overarching objectives of cyber adversaries. Examples of tactics include Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, and many more.
-
Techniques: Within each tactic, MITRE ATT&CK outlines specific techniques that adversaries employ to achieve their objectives. Techniques represent the specific actions, tools, and procedures used by attackers. Examples include Spearphishing, Exploit Public-Facing Application, Lateral Movement, Data Exfiltration, and more.
-
Sub-Techniques: MITRE ATT&CK further breaks down techniques into sub-techniques, providing a more granular view of adversary behavior. Sub-techniques represent variations or specific implementations of techniques and help to capture the ever-evolving tactics used by adversaries.
Pilars of MITRE ATT&CK:
-
Adversary-Centric Approach: MITRE ATT&CK takes an adversary-centric approach, focusing on the techniques and tactics employed by real-world attackers. This perspective allows organizations to understand and simulate the behaviors and strategies of adversaries, enabling proactive defense measures.
-
Improved Threat Intelligence: By leveraging MITRE ATT&CK, organizations gain valuable insights into the tactics and techniques most commonly used by adversaries. This knowledge enhances threat intelligence capabilities, enabling security teams to anticipate and respond to emerging threats effectively.
-
Detection and Prevention: MITRE ATT&CK serves as a valuable resource for developing robust detection and prevention mechanisms. Organizations can align their security controls, such as Intrusion Detection Systems (IDS), Security Information and Event Management (SIEM) platforms, and Endpoint Detection and Response (EDR) tools, with the techniques outlined in MITRE ATT&CK, enhancing their ability to detect and mitigate attacks.
-
Red Team Exercises and Purple Teaming: MITRE ATT&CK is frequently employed in red team exercises and purple teaming engagements. Red teams simulate real-world attacks using the techniques documented in MITRE ATT&CK, while blue teams validate their defensive capabilities against these simulated attacks. This collaborative approach fosters continuous improvement in an organization’s security posture.
Conclusions.
In this short post we have taken a look at Mitre and I hope you found it interesting. As I always say this is just the beginning of your research and I advise you to take a look at their website. Apart from Mitre, it would be interesting for you to take a look at Cyber Kill Chain and Diamond Model.
Have a nice day!