LLVM for Malware Obfuscation

Introduction
In the constantly evolving landscape of cybersecurity, malicious actors seek to evade detection and analysis through various means, one of which is malware obfuscation. This blog post delves into the world of LLVM (Low-Level Virtual Machine) and explores how it can be harnessed to enhance malware obfuscation techniques, making it more challenging for security researchers and analysts to identify and combat malicious code effectively.
Understanding LLVM: A Brief Overview
LLVM, originally an acronym for “Low-Level Virtual Machine,” is an open-source compiler infrastructure project. It provides a set of modular and reusable compiler and toolchain technologies, designed to optimize program compilation and execution efficiently. Initially developed for C and C++ languages, LLVM has now expanded its support to multiple programming languages, making it versatile and widely adopted within the development community.
The Role of LLVM in Malware Obfuscation
Malware authors have increasingly turned to LLVM as a powerful tool to obfuscate their malicious code. By leveraging LLVM, attackers can achieve two primary objectives:
-
Code Transformation: LLVM’s intermediate representation (IR) enables transforming the original source code into an intermediate form, which can be further optimized and modified. This transformation process makes the malware’s behavior less obvious and hinders signature-based detection mechanisms.
-
Polymorphic Code Generation: LLVM allows for the generation of polymorphic code, where the same malicious function or routine is represented in multiple, slightly varying forms. Each instance of the code behaves similarly but appears different, thwarting pattern-based detection techniques.
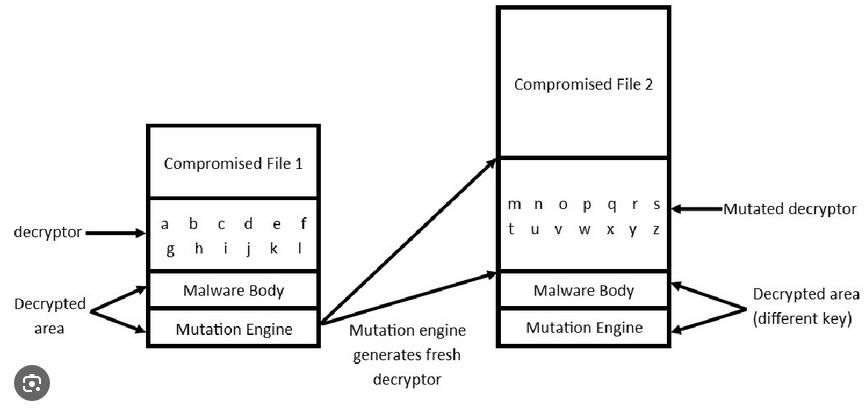
Obfuscation Techniques Enabled by LLVM
Various obfuscation techniques can be facilitated using LLVM. Some notable ones include:
-
Control Flow Flattening: This technique disrupts the natural flow of code by converting conditional branches into a sequence of unconditional jumps, making it difficult for analysts to follow the execution path.
-
Instruction Substitution: Malware authors can replace standard instructions with semantically equivalent, yet different, instructions to evade signature-based detection systems.
-
Register Renaming: By renaming registers and variables, malware authors can further obfuscate their code and make it harder to understand the program’s intentions.
-
Dead Code Insertion: Inserting redundant code that does not affect the malware’s functionality helps confuse analysts, leading them away from the actual malicious routines.
Challenges in Malware Analysis with LLVM-based Obfuscation
The adoption of LLVM for malware obfuscation presents significant challenges for cybersecurity researchers:
-
Reduced Readability: The transformed IR code can become convoluted and challenging to comprehend, demanding extensive efforts to reconstruct the original intent.
-
Dynamic Behavior: Polymorphic code generated by LLVM introduces variability in the malware’s runtime behavior, evading signature-based detection approaches.
-
Sophistication Levels: As malware authors continue to refine their obfuscation techniques, security analysts must continuously enhance their skills and toolsets to detect these advanced threats.
Mitigating LLVM-based Obfuscation
While dealing with LLVM-obfuscated malware poses challenges, there are several strategies that security professionals can employ:
-
Behavior-Based Analysis: Instead of relying solely on signatures, focus on monitoring and analyzing the malware’s behavior to detect anomalies.
-
Heuristic Approaches: Develop heuristics that identify common obfuscation patterns seen in LLVM-obfuscated malware.
-
De-Obfuscation Tools: Create and enhance tools that can reverse engineer LLVM-obfuscated code, aiding in its analysis.
Conclusion
The rise of LLVM in malware obfuscation presents both opportunities and challenges for the cybersecurity community. Malicious actors exploit the flexibility and power of LLVM to create sophisticated and stealthy malware, necessitating continuous efforts to improve detection and analysis techniques. By staying abreast of the latest advancements in obfuscation and investing in innovative defensive mechanisms, security professionals can effectively combat the ever-evolving threat landscape and safeguard digital assets from stealthy malware attacks.