You must learn LDAP (Lightweight Directory Access Protocol) !

1 What is LDAP and what is it used for?
LDAP is a TCP/IP application layer protocol that allows access to an ordered and distributed directory service to search for any information in a network environment. LDAP is an access protocol that allows us to access local network resources without the need to create different users in the operating system, and is much more versatile. For example, LDAP allows to perform authentication and authorization tasks to users of different software such as Docker, OpenVPN and many more uses.
LDAP can be used both by a user who is asked for access credentials, and by applications to know if they have access to certain system information or not. Generally an LDAP server is located in a private network.
2 LDAP Server.
LDAP is a protocol that has a client-server architecture, therefore, we will have several clients connecting to one or more LDAP servers. Generally, a single LDAP server is used to which tens or hundreds of clients will connect to access the different resources of the local network.
The operation of LDAP is quite simple, as the communication is like any other communication between a client and a server. The following are the most important steps of the communication:
- The client connects to the LDAP server through port 389 and initiates the LDAP session.
- Both establish a connection.
- Data is exchanged.
What can we do when we are authenticated?
We can read information about a directory, although the server will check if we have access to that information. Then we can modify information and the server will check if we have permissions to make modifications.
These are the main actions we can perform, but let’s list all the operations we can perform:
- Add: we can add a new entry.
- Modify: modify an entry.
- Delete: delete an entry.
- Search: search for entries in a directory.
- Compare: check a specific attribute.
- Abort: abort an action.
- Bind: authenticate to the server.
- Initiate TLS: establish a secure connection.
- Unbind: close the connection.
3 Types of authentication.
Let’s check the different types of authentication that we can perform on an LDAP server:
- Anonymous: This is the least secure authentication. The accounts of users attempting to access a service are stored in public LDAP databases.
- Simple: This system is based on combinations of names, whose username and password are delivered unencrypted in many cases in plain text.
- SASL: This is the most secure authentication mechanism against LDAP. This type can be integrated into some mechanisms such as TLS or Kerberos on servers.
4 Structure and components.
In order for this protocol to do its job, there is a structure of directories and components. The most important components are
- Directories: is a tree of directory entries.
- Entries: consists of a set of attributes. Entries describe the user by listing all their attributes. Each entry has a unique identifier with its DN (Distinguished Name).
- Attributes: attributes have a name and one or more values, they are defined in schemas.
A basic LDAP structure could be as follows
- dn (Distinguished Name): is the name of the entry, but it is not an attribute nor is it part of the entry itself.
- cn (Common Name): is the relative Distinguished Name.
- dc (Domain Component): is the Distinguished Name of the parent entry.
5 Installation.
If we are on a Linux based system we can install it using the following command :
sudo apt install slapd ldap-utils
We provide the sudo password and then we get a screen where we enter the administrator password of our choice.
To check if it is installed we can use the following command that will display the following information.
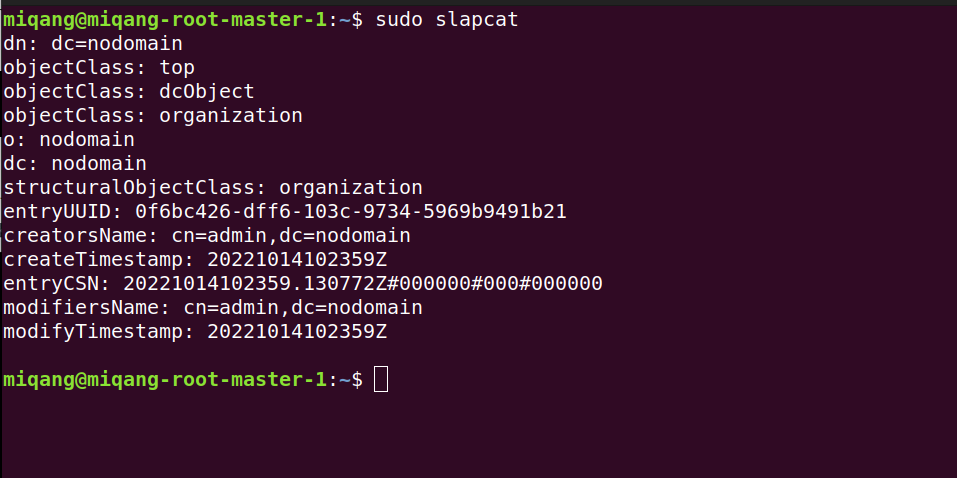
To start configuring the LDAP we enter the following command.
sudo dpkg-reconfigure slapd
Then a pop up appears and we just enter the dns and the name of our organization. We can use slapcat again to check that we entered the data correctly, now we just enter a list of the users creating a file.
sudo touch /etc/ldap/users.ldif
The contents of the file are as follows:
- dn: ou=people,dc=example,dc=com objectClass: organizationalUnit ou: people
Where example is your domain.
To enter the data we carry out the following command, it will ask us for the administrator password, we provide it:
sudo ldapadd -D cn=admin,dc=glaucoma,dc=com -W -H ldapi:/// -f /etc/ldap/users.ldif
We can perform a search of what we have provided:
sudo ldapsearch -x -b dc=glaucoma,dc=com ou
Conclusions.
The LDAP protocol is widely used in professional environments to authenticate different users, and where we can store information in an orderly and hierarchical manner. I hope you found it interesting and as we always recommend, go out, investigate and practice as much as you can!
Thank you for reading!