All started with Glaucoma
Glaucoma is considered the first Spanish hacker group. They were active between 1987 and 1989. They are known as Glaucoma because they attacked the Iris network, a research network, and through the university computers they jumped to the world and to history as the first hackers recognized in Spain.
Continue reading more in this blog...
Cybersecurity
Main category addressed in this blog. We will talk about news, certifications, tools, red team, blue team and much more.
Linux
I like Linux and learning about it. If you want to get into IT you must learn Linux!.
Networks & Protocols
Understand how different devices are connected and the protocols they use.
Recent Posts

Securing Your Connections with SSH
While SSH is renowned for its security prowess, its utility extends far beyond mere encryption. Let's explore some of the powerful functionalities SSH offers.
Protocols

Welcome to Docker
Docker serves as a transformative platform in software development, employing containers as self-contained entities that comprehensively encapsulate applications along with their requisite dependencies. These containers, akin to standardized and portable units, exhibit consistent behavior across diverse computing environments, fostering simplified development, deployment, and scaling processes.
Containers

Hardening ubuntu server
Have a look at a small ubuntu hardening guide.
Hardening
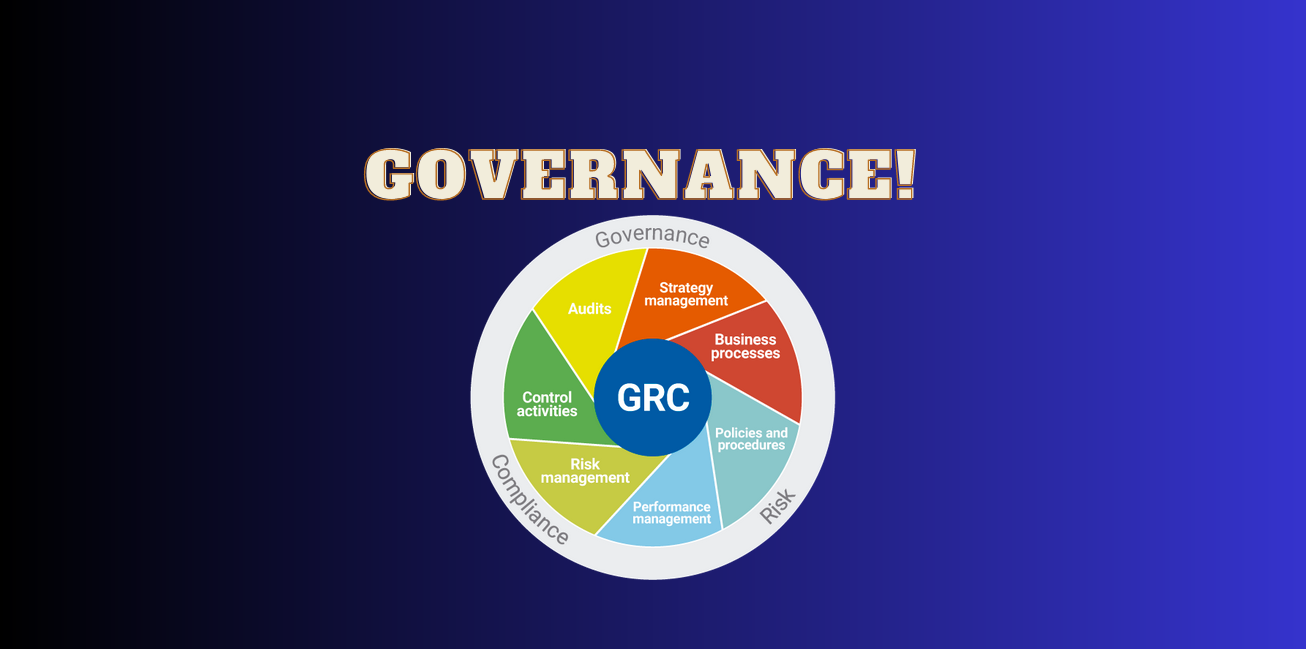
Governance?
Cybersecurity governance involves the orchestration of policies, risk management, and organizational structures to fortify digital resilience and align security strategies with business objectives.
Standards/Data

A Comprehensive Guide to IRM, DLP, MDM, and CASB
IRM, DLP, MDM, and CASB: Unveiling the dynamic quartet reshaping cybersecurity, from empowering data ownership to safeguarding against unintended exposure and navigating the complexities of mobile and cloud security.
Standards/Data

A Deep Dive into Privacy-Preserving Computation
In the world of cybersecurity, four prominent standards—PTES, OSSTMM, NIST, and OWASP—stand as pillars of guidance.
Standards/Data
Who's behind Gl4uc0m4 ?
My name is Miguel (aka Tempest) and I'm a software engineer with a master's degree in cybersecurity.
This project arises as my own challenge to prove myself that I am able to create content about what I am passionate. I hope you find my content useful!
Posts by tag
Greetings
Information Gathering
Attacks
Protocols
Linux
Dev
Firewalls
Cryptography
DFIR
- File type formats and Magic Numbers for Digital forensics & Malware Analysis
- Digital Forensics & Incident Response
Standards/Frameworks
- Cybersecurity Standards: PTES, OSSTMM, NIST, and OWASP
- Decoding CVSS: Prioritizing Vulnerability Security
- Cybersecurity Toys. 90 % OFF
- Mitre ATT&CK!!!
SOC
Malware
Virtualization
Windows
Vulnerability
Standards/Data
- Governance?
- A Comprehensive Guide to IRM, DLP, MDM, and CASB
- A Deep Dive into Privacy-Preserving Computation
- States of Data